Introduction
The Role of 5G and Network Sharing
The rollout of 5G technology is a major milestone in how we stay connected. It brings faster speeds, greater reliability, and more efficient communication. This new generation of technology is transforming industries, enabling things like real-time communication for self-driving cars, smart cities, and automated factories. However, building and managing 5G networks can be costly and complex.
That’s where the Multi-Operator Core Network (MOCN) comes in. MOCN allows multiple network operators to share the same Radio Access Network (RAN) infrastructure while keeping their core networks separate. This makes it a cost-effective solution for rolling out 5G. By sharing resources, operators can save money and expand coverage without losing control over their individual services.
In fact, MOCN adoption is growing quickly. By 2025, around 30% of mobile networks worldwide are expected to use MOCN to handle the growing demand for 5G services.
Why Is Securing N2 and N3 Interfaces Critical in MOCN Networks?
While MOCN offers many benefits, it also comes with unique challenges—especially when it comes to securing the N2 and N3 interfaces, which are key components of a 5G network.
- The N2 interface connects the RAN (gNB) to the Access and Mobility Management Function (AMF) in the core network. It handles important tasks like signaling and managing user mobility.
- The N3 interface connects the RAN to the User Plane Function (UPF) in the core network, allowing user data to flow between devices and the internet.
In a shared MOCN setup, these interfaces face specific risks:
- Cross-operator interference: If traffic isn’t properly isolated, data could leak between operators.
- Data breaches: Without strong encryption, attackers could intercept sensitive signaling (N2) or user data (N3).
- Signaling hijacking: Hackers might exploit insecure N2 interfaces to reroute or disrupt network traffic.
This raises the critical question: how is N2 and N3 security handled in MOCN networks? Addressing this requires robust solutions like encryption, authentication, and traffic isolation to ensure data stays safe and operators remain independent. With strong security measures, MOCN can deliver its cost and coverage benefits without putting networks or users at risk.
Table of Contents
- Understanding MOCN Network Architecture
- How Is N2 and N3 Security Handled in MOCN Networks?
- Challenges in Securing N2 and N3 in MOCN Networks
- Solutions and Best Practices for N2 and N3 Security
- Real-World Implementations and Case Studies
- Frequently Asked Questions
- Conclusion
Understanding MOCN Network Architecture
What Is MOCN and How Does It Work?
Multi-Operator Core Network (MOCN) is a 5G network-sharing solution that allows multiple operators to use the same Radio Access Network (RAN) infrastructure while maintaining their own independent core networks1. It is one of the most efficient ways to deploy 5G networks, particularly in areas where setting up separate infrastructures is impractical or cost-prohibitive.
The MOCN model works by enabling operators to share RAN components, such as base stations, antennas, and spectrum resources, while ensuring traffic remains segregated and securely routed to the respective operator’s core network2. This makes MOCN a preferred choice for cost optimization and efficient use of network resources.
Advantages of MOCN in 5G:
- Cost Sharing: Operators can split the expenses of infrastructure deployment and maintenance.
- Resource Efficiency: Spectrum and hardware resources are used more effectively, reducing waste.
- Faster Deployment: Sharing RAN infrastructure speeds up network rollout in new or underserved areas.
How Operators Share the RAN While Maintaining Independent Core Networks
MOCN achieves operator-specific traffic separation using Public Land Mobile Network Identifiers (PLMN IDs). Each operator is assigned a unique PLMN ID, which helps identify and route user traffic to the correct core network. The RAN, which is shared by all participating operators, ensures traffic segregation by logically isolating users based on their assigned PLMN ID.
For example:
- A user belonging to Operator A will have their traffic routed through the shared RAN to Operator A’s core network.
Similarly, users of Operator B and Operator C will have their traffic securely routed to their respective cores without interference.
Key Interfaces in MOCN Networks
In MOCN architecture, two critical interfaces ensure seamless communication between the RAN and the core network3:
- N2 Interface:
- Connects the gNB (RAN) to the Access and Mobility Management Function (AMF) in the core network.
- Handles signaling and mobility management tasks, such as user registration and session setup.
- Example: When a user moves between cell towers, the N2 interface ensures a smooth handover.
- N3 Interface:
- Connects the gNB (RAN) to the User Plane Function (UPF) in the core network.
- Transfers user data (e.g., web browsing, video streaming) between the RAN and the internet.
- Example: The N3 interface handles high-speed data flows, ensuring low latency for 5G applications.
Illustration: Diagram of N2 and N3 Interfaces in MOCN Architecture
To visualize the MOCN architecture:
Shared RAN
│
┌──────────┴──────────┐
│ │
N2 (Signaling) N3 (User Data)
│ │
┌───────┴───────┐ ┌─────┴─────┐
│ │ │ │
AMF (Core A) AMF (Core B) UPF (Core A)
UPF (Core B)
This diagram shows how N2 and N3 interfaces connect the shared RAN to each operator’s independent core network.
How Is N2 and N3 Security Handled in MOCN Networks?
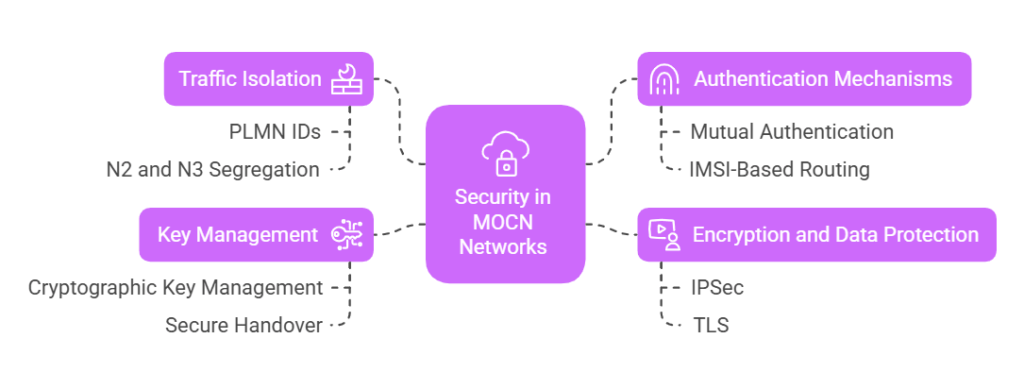
Traffic Isolation and Logical Separation
In MOCN networks, traffic isolation is critical to maintaining the independence and security of each operator sharing the RAN. This is achieved through logical separation of signaling and user data, ensuring each operator’s traffic remains distinct and secure.
- Use of PLMN IDs:
- Each operator is assigned a unique Public Land Mobile Network Identifier (PLMN ID).
- The shared RAN uses these identifiers to route traffic to the correct operator core, preventing cross-operator interference or data leaks.
- Logical Segregation of N2 and N3 Traffic:
- N2 (Control Plane): Handles signaling traffic, such as user registration and session setup, and is logically separated to ensure each operator can manage its users securely.
- N3 (User Plane): Transports user data such as web traffic and video streams. Logical pathways ensure data from one operator does not interfere with or leak into another operator’s traffic.
Authentication Mechanisms
Authentication is essential to ensure that only legitimate users and devices can access the network, especially in a shared MOCN environment.
- Mutual Authentication:
- The gNB (RAN) and each operator’s core components (AMF and UPF) mutually authenticate each other using cryptographic protocols.
- This process ensures the RAN connects only to authorized core networks, preventing unauthorized access or man-in-the-middle attacks.
- IMSI-Based Routing:
- The International Mobile Subscriber Identity (IMSI), embedded in user devices, is used to identify the operator a subscriber belongs to.
The RAN uses this information to validate users and securely route their traffic to the appropriate operator’s core network.
Encryption and Data Protection
Strong encryption protocols are used to protect both signaling and user data in MOCN networks.
- Application of IPSec/TLS:
- IPSec (Internet Protocol Security) and TLS (Transport Layer Security) protocols are widely used to secure N2 and N3 traffic.
- IPSec is ideal for securing user data on the N3 interface, while TLS protects signaling traffic on the N2 interface.
- Why These Protocols Work Well:
- Confidentiality: Encrypts traffic to prevent unauthorized access.
- Integrity: Ensures that the data is not altered during transmission.
- Scalability: Both protocols are robust enough to handle the high-speed, high-volume traffic of 5G networks.
Key Management and Secure Handover
Effective management of cryptographic keys is critical for maintaining security across shared networks and ensuring seamless user mobility.
- Cryptographic Key Management:
- Each operator manages its own encryption keys, ensuring that data remains secure and isolated even within the shared RAN.
- Keys are dynamically generated and rotated to prevent compromise.
- Secure Handover:
- When a user moves between cell towers, the N2 interface ensures that signaling remains uninterrupted.
Simultaneously, the N3 interface secures user data during the handover, ensuring continuity without compromising security.
Examples of Security Implementations
1.Ericsson4:
- Ericsson implements advanced encryption and authentication mechanisms for MOCN. Their solutions use AI-driven analytics to monitor traffic for anomalies, further strengthening N2 and N3 security.
2.Parallel Wireless5:
- Parallel Wireless leverages OpenRAN technology to provide robust security for MOCN networks. They emphasize logical traffic segregation and end-to-end encryption using IPSec and TLS.
3.3GPP Standards6:
The 3GPP Rel-19 standards for network sharing outline enhancements for traffic isolation, secure routing, and encryption.
Challenges in Securing N2 and N3 in MOCN Networks
The N2 and N3 interfaces are critical to the operation of 5G MOCN networks, but securing them presents unique challenges due to the shared infrastructure and multi-operator setup. These challenges include multi-tenant risks, operational hurdles, and specific threats to the control and user planes.
Multi-Tenant Risks in Shared Networks
- Shared Infrastructure Vulnerabilities:
- In an MOCN network, multiple operators share the same Radio Access Network (RAN). This setup increases the risk of cross-operator vulnerabilities, where a misconfiguration or compromise in one operator’s system could affect others.
- A shared RAN also creates opportunities for attackers to exploit vulnerabilities in common components like gNBs (base stations) to gain access to multiple networks.
- Risks from Misconfigured or Rogue Operators:
- A poorly configured system or a rogue operator within the MOCN setup could inadvertently or intentionally disrupt traffic isolation mechanisms.
- This could lead to traffic leakage, where data from one operator is exposed to another, violating privacy and security requirements.
Operational and Regulatory Challenges
- Compliance with Standards:
- MOCN operators must comply with stringent standards like 3GPP specifications to ensure interoperability and security. Additionally, they must adhere to regulations such as the General Data Protection Regulation (GDPR) to protect user data privacy.
- Non-compliance can result in legal penalties and loss of customer trust.
- Balancing Security, Performance, and Costs:
- While robust security measures like encryption and traffic isolation are essential, they can increase complexity and cost.
- Operators must carefully balance security with network performance to maintain low latency and high-speed data delivery, key features of 5G.
Specific Risks
- Signaling Hijacking on N2:
- The N2 interface handles signaling between the gNB and the AMF. If attackers gain access, they could hijack signaling messages, disrupt session management, or reroute user traffic.
- For example, signaling hijacking could result in unauthorized users gaining access to network resources, affecting service availability.
- Data Breaches on N3:
- The N3 interface transfers user data between the gNB and the UPF. Without proper encryption, this data is vulnerable to interception, leading to data breaches.
- Sensitive information like personal user data or application traffic could be exposed, violating user privacy.
- Real-World Example of Security Breaches in Shared Networks: Securing N2 and N3 interfaces in MOCN networks requires a proactive approach to mitigate these challenges. Operators must implement stringent isolation mechanisms, robust encryption, and rigorous compliance protocols to ensure that shared infrastructures remain secure and resilient against evolving threats.
Solutions and Best Practices for N2 and N3 Security
Traffic Segregation Techniques
- Use advanced routing and segmentation (e.g., VLANs) to isolate traffic at the network level.
Implement network slicing, which creates virtual network segments for each operator, isolating functions securely while maintaining operational flexibility.
Enhanced Authentication and Access Control
- Deploy stronger mutual authentication mechanisms like public key infrastructure (PKI) for identity verification.
- Utilize AI-based anomaly detection systems to monitor access patterns and prevent unauthorized entry by detecting unusual activity in real time.
Encryption and Monitoring
- Apply IPSec and TLS protocols (as discussed earlier) to encrypt both control (N2) and data (N3) traffic.
- Leverage AI-driven monitoring tools to analyze traffic continuously and flag suspicious patterns, such as abnormal signaling behavior or packet injection attempts.
Future Enhancements in 5G Security
- 3GPP Rel-19 Updates:
- Improved standards for network slicing, traffic isolation, and key management.
- Enhanced signaling security mechanisms to address emerging threats in shared networks.
- Adoption of Zero Trust Models:
- This model treats every user, device, and connection as untrusted by default, requiring continuous verification at all access points. It ensures that even if part of the network is compromised, attackers cannot move laterally to other components.
Real-World Implementations and Case Studies
Security in MOCN Deployments by Major Vendors
- Ericsson’s RAN and Core Security Solutions for MOCN7
Ericsson has been a leader in providing robust security frameworks for MOCN networks. Their solutions integrate:- AI-Driven Security: Ericsson uses machine learning algorithms to monitor network behavior and identify anomalies in real time, bolstering security for N2 and N3 interfaces.
- End-to-End Encryption: Both signaling (N2) and user data (N3) are protected using advanced encryption protocols like IPSec and TLS, ensuring data integrity and confidentiality.
- Multi-Tenant Isolation: By leveraging logical segregation through PLMN IDs and network slicing, Ericsson ensures that traffic from different operators remains isolated within the shared RAN.
Key Insight: Ericsson’s focus on automation and AI has been instrumental in mitigating threats in complex MOCN environments. Their approach demonstrates how proactive monitoring can reduce operational risks.
2.Parallel Wireless and OpenRAN for Secure MOCN8
Parallel Wireless has been at the forefront of implementing OpenRAN solutions that enhance MOCN security.
- Modular and Flexible Design: OpenRAN architecture allows for dynamic integration of security tools, ensuring that operators can adapt to evolving threats.
- Logical Traffic Segregation: The use of PLMN IDs and unique routing mechanisms ensures that operator-specific traffic remains isolated.
- Cost-Effective Encryption: Parallel Wireless leverages cost-efficient encryption techniques, such as optimized IPSec configurations, to ensure secure user data transmission without significant performance trade-offs.
Key Insight: OpenRAN-based MOCN deployments highlight how flexible and modular designs can enhance security while reducing deployment costs.
Lessons Learned from 5G Network Sharing Projects
Best Practices Observed in Live Deployments:
Comprehensive Traffic Monitoring: Many successful deployments use AI-based tools to continuously monitor traffic for anomalies, ensuring real-time threat detection.
Effective Key Management: Dynamic key rotation has proven effective in reducing vulnerabilities associated with static encryption keys.
Compliance with Standards: Adherence to 3GPP and local data protection regulations like GDPR ensures that shared networks meet global security requirements.
Challenges Encountered:
Complexity of Multi-Tenant Environments: Coordinating security across multiple operators in a shared RAN can be challenging, especially when one operator’s configuration inadvertently impacts others.
Balancing Costs and Security: Operators often face difficulties in implementing robust security measures without exceeding budget constraints.
Comparison of Successful Implementations and Areas for Improvement
- Successful Implementations:
- Ericsson: Emphasis on automation and AI has significantly reduced response times to potential threats.
- Parallel Wireless: Flexible OpenRAN architectures have enabled cost-effective yet secure MOCN deployments.
- Areas for Improvement:
- Inter-Operator Coordination: More standardized processes are needed to ensure seamless coordination among operators sharing the same RAN.
- Advanced Handover Security: Improving security during user mobility events remains a key focus area, especially in high-density urban environments.
Frequently Asked Questions
1. What is MOCN in 5G, and why is it important?
MOCN (Multi-Operator Core Network) allows multiple operators to share the same RAN (Radio Access Network) while maintaining independent core networks. It reduces costs, speeds up 5G deployment, and improves spectrum utilization, especially in rural or high-cost areas.
2. How is N2 and N3 security handled in MOCN networks?
N2 (control plane) and N3 (user plane) are secured through:
- Encryption: IPSec for user data (N3) and TLS for signaling (N2).
- Traffic Isolation: PLMN IDs separate operator traffic.
- Authentication: IMSI-based routing and mutual authentication protect data and ensure only authorized access.
3. What are the main challenges in securing shared 5G infrastructures?
Key challenges include:
- Cross-Operator Risks: Traffic leaks or interference due to misconfigurations.
- Compliance: Meeting GDPR and 3GPP standards.
- Cost vs. Security: Balancing affordability with robust protection.
- Emerging Threats: Sophisticated attacks like signaling hijacking.
4. What future trends are expected in MOCN network security?
Upcoming trends:
- AI-Based Monitoring: Detects threats in real-time.
- Zero Trust Models: Strengthens access control.
- 3GPP Rel-19 Updates: Improved isolation and encryption.
- Quantum-Resistant Encryption: Prepares for future quantum computing threats.
Conclusion
Securing N2 and N3 interfaces is essential for ensuring the smooth and safe operation of MOCN networks. These interfaces play a critical role in separating control and user data traffic while maintaining the independence of multiple operators sharing the same infrastructure. Robust security measures, such as encryption, traffic isolation, and advanced authentication, not only protect sensitive data but also build trust among operators and end users. Addressing the question of “how is N2 and N3 security handled in MOCN networks“ highlights the importance of adopting proven techniques like IPSec, TLS, and AI-driven monitoring to mitigate risks and enhance reliability.
As the telecom landscape evolves, MOCN security must keep pace with emerging challenges and technologies. Future advancements, such as Zero Trust models, quantum-resistant encryption, and 3GPP Rel-19 updates, will shape the way networks handle shared infrastructure security. Operators and developers are encouraged to embrace these innovations and implement best practices to ensure that MOCN remains a secure, scalable, and efficient solution for the 5G era and beyond.
