In today’s digital world, the stakes for software security are sky-high. Imagine pouring countless hours into developing Endbugflow software, only for it to be hacked, misused, or stolen. Knowing how Endbugflow software can be protected isn’t just a matter of preventing financial loss—it’s about keeping your reputation strong, staying compliant with regulations, and securing your business for the long term. This guide covers everything you need to know about protecting your software, from legal safeguards to technical defenses.
Why Endbugflow Software Needs Protection
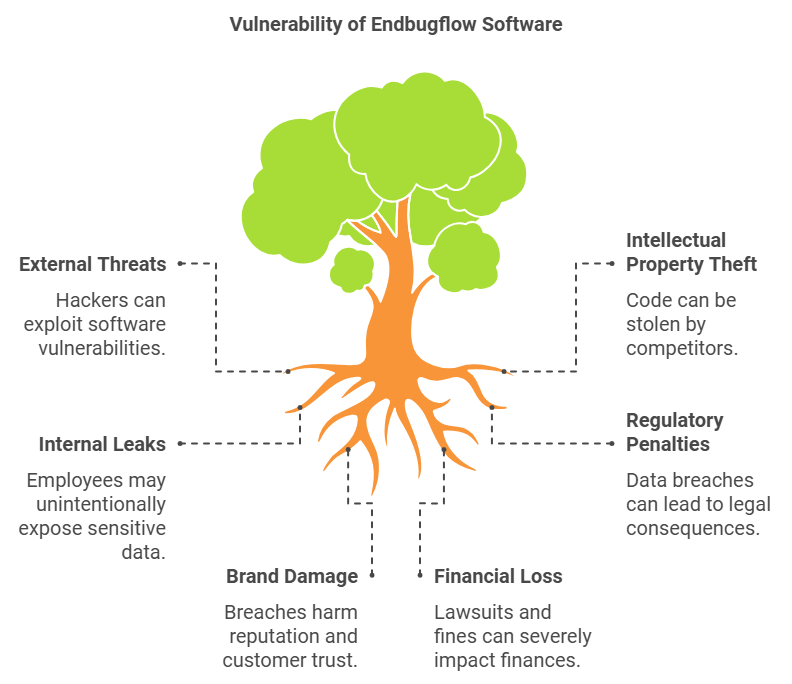
The Importance of Protection
Before diving into how Endbugflow software can be protected, let’s explore why it’s so crucial. Your software is a valuable asset, vulnerable to threats like hackers, intellectual property thieves, and even internal leaks. If unauthorized parties gain access to your code, they could exploit vulnerabilities, steal sensitive data, or undermine your competitive edge. Data breaches can also lead to regulatory penalties and damage to your brand.
Real-World Impact: Remember when major companies like Equifax and Marriott suffered data breaches? The aftermath included lawsuits, fines, and a massive hit to their reputation. For smaller software companies, the consequences can be even more dire.1
9 Methods to protect Endbugflow software
- Legal Protection Methods for Endbugflow Software
- Technical Security Measures for Endbugflow Software
- Training and User Awareness
- Layered Security Approach
- Future-Proofing Endbugflow Software Security
- Compliance and Legal Considerations
- Practical Developer Tips
- Leveraging Community Resources
- Real-World Examples
Legal Protection Methods for Endbugflow Software
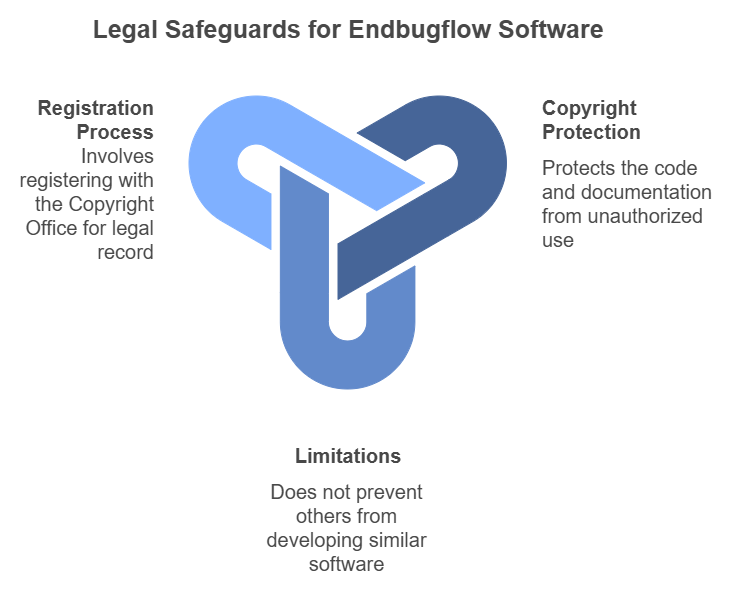
A solid understanding of intellectual property law is essential when discussing how Endbugflow software can be protected. Here’s how to legally safeguard your software.
Copyright Protection
Copyrights form the bedrock of software protection, safeguarding the code and documentation.
Limitations: Copyright only covers the literal code and doesn’t prevent others from developing similar software based on the same concepts. That’s why additional protections are necessary.
What It Covers: Copyright laws protect the exact way you’ve written your code, preventing others from copying or distributing it without your permission. However, they don’t cover the underlying functionality or concepts.
How to Register: To get copyright protection in the U.S., register with the Copyright Office. This creates a legal record of your ownership, which makes it easier to enforce your rights in court. Registration is affordable and straightforward.2
Patents for Unique Features
If Endbugflow has innovative features, patents offer another layer of protection.
Benefits: A successful patent gives you exclusive rights to your software’s features, preventing others from using or selling them without your consent.
What’s Patentable: Software patents can be tricky. Generally, only unique processes or methods that solve a specific technical problem qualify. Your software’s patentable aspects must be novel and non-obvious.
Challenges and Tips: The Alice Corp. v. CLS Bank ruling made software patents harder to secure, especially for abstract ideas. To increase your chances, work with a patent attorney to clearly define how your software offers a unique technical solution.3
Trade Secrets
Certain elements of Endbugflow, like algorithms and proprietary processes, are best protected as trade secrets.
Securing Trade Secrets: Trade secrets are only protected if you actively keep them secret. Use NDAs with employees and partners, restrict access to sensitive information, and monitor who has access. Encryption and secure data storage also help maintain confidentiality.
What to Protect: Anything that gives you a competitive edge and isn’t publicly disclosed can qualify. Examples include data analysis methods, client data management strategies, and proprietary algorithms.4
Licensing Agreements
Licensing agreements specify how your software can be used, adding another layer of legal protection.
Key Clauses: Include terms that prohibit reverse engineering, sublicensing, and distribution. Specify the scope of use, such as the number of devices or users allowed. Clearly outline the consequences of breaking the agreement, such as financial penalties or license termination.
Why Licensing Matters: A well-crafted license agreement restricts unauthorized use, sharing, and modification of Endbugflow. This is essential when distributing software to clients or partners.
Technical Security Measures for Endbugflow Software
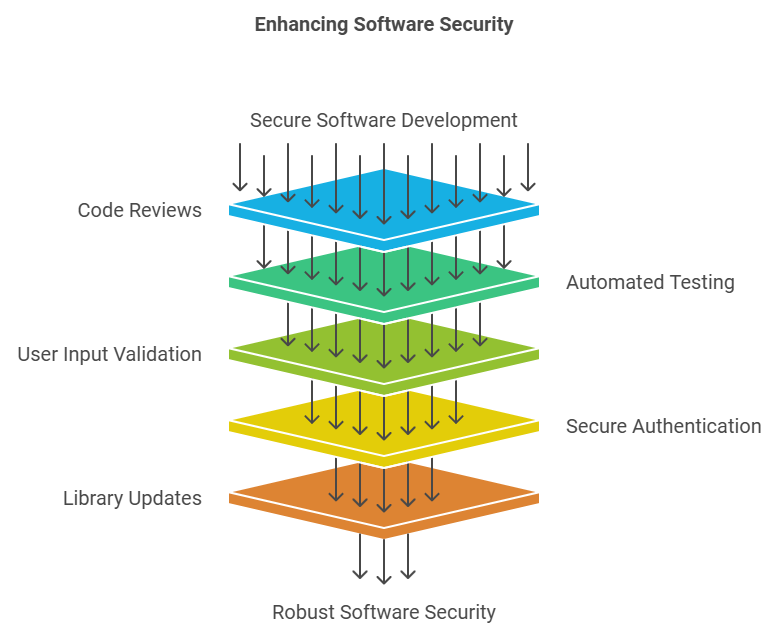
To fully understand how Endbugflow software can be protected, you need to implement technical measures alongside legal ones.
Secure Software Development Practices
Developing secure software starts with secure coding practices.
Code Reviews and Testing: Regular code reviews can catch mistakes and security flaws early. Use automated tools for static code analysis and manual testing to ensure comprehensive coverage.
Best Practices: Always validate user input to avoid injection attacks, use secure authentication methods, and never store sensitive information in plain text. Keep libraries and frameworks up-to-date to prevent vulnerabilities from older versions.
Encryption Techniques
Encryption protects sensitive data, making it unreadable to unauthorized users.
Data Masking and Tokenization: These techniques further secure sensitive information. Data masking hides personal data, while tokenization replaces it with tokens that can only be mapped back to the original data in a secure environment.
How It Works: Use symmetric encryption for data stored on servers, and asymmetric encryption for data exchanged over networks. Modern encryption standards like AES-256 provide robust protection.
Code Obfuscation
Code obfuscation transforms your code into a form that’s difficult to understand or reverse-engineer.
- Why It’s Important: Even if someone gains access to your code, obfuscation makes it nearly impossible to decipher. This protects your proprietary algorithms and methods.
How to Implement: Use obfuscation tools that rename variables, obscure logic, and make the code structure complex.
Continuous Monitoring and Threat Detection
Real-time monitoring allows you to respond to threats immediately.
Incident Response Plan: Prepare a detailed plan outlining what to do if a breach occurs. This should include steps to contain the damage, notify affected parties, and investigate the incident.
What to Monitor: Set up intrusion detection systems (IDS) and monitor logs for suspicious activities. Use automated tools to flag unusual behavior, such as multiple failed login attempts or unauthorized data access.
Training and User Awareness
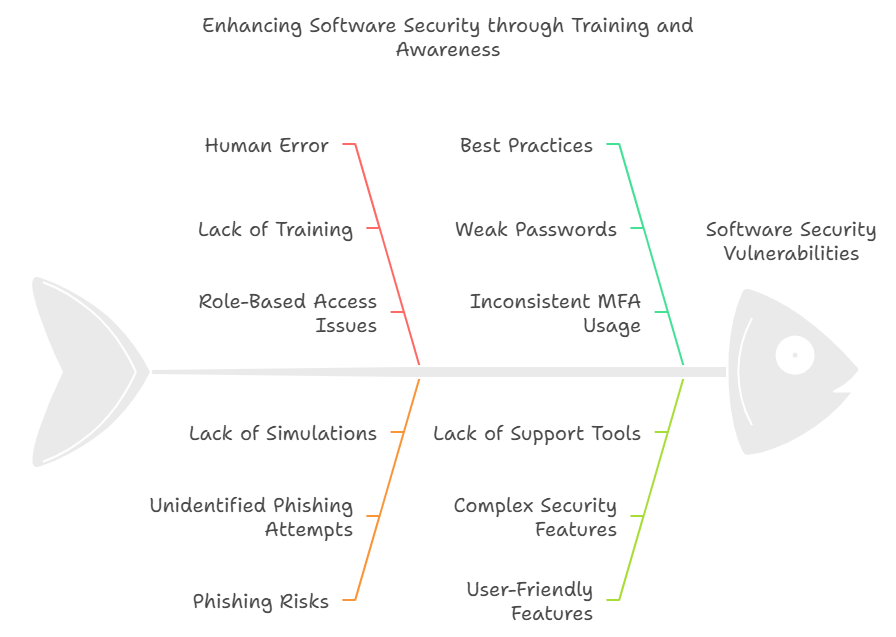
Another critical aspect of how Endbugflow software can be protected is educating your team and users.
Educating Employees and Users
Human error is one of the biggest security risks. Training your team reduces this risk.5
Role-Based Access: Limit access to sensitive parts of the software. Employees should only have access to the data they need to perform their jobs.
Phishing Awareness: Teach your team how to identify phishing emails and scams. Regularly run simulations to keep them sharp.
Best Practices: Emphasize the importance of strong passwords, multi-factor authentication (MFA), and secure device usage. Simple habits, like locking screens when away from the computer, can make a big difference.
User-Friendly Security Features
If security features are too complex, users may bypass them.
Simplifying MFA: Use easy-to-implement options like mobile-based verification. Provide password managers to help users create and store strong passwords securely.6
Layered Security Approach
A multi-layered approach ensures Endbugflow software stays secure, even if one measure fails.
Why Multiple Layers Matter
Using a combination of encryption, licensing, code obfuscation, and secure coding practices creates a defense-in-depth strategy. If one layer is breached, others still protect your software.
Future-Proofing Endbugflow Software Security
Adaptive Security with AI and Machine Learning
AI technology can identify threats faster and adapt to new attack methods.
- Why It’s Effective: AI can analyze user behavior and detect anomalies that human monitors might miss. Machine learning models improve over time, becoming better at spotting and preventing attacks.
Regular Updates and Patch Management
Always keep your software and its dependencies up-to-date.
Automating Updates: Automation ensures updates are applied promptly, minimizing the window of opportunity for attackers. Use dependency management tools to track and update libraries.
Staying Compliant with Evolving Regulations
Laws change, and so do data protection requirements. Regularly review your software to ensure it complies with global regulations like GDPR and CCPA.7
Compliance and Legal Considerations
Following Data Privacy Laws
Failing to follow laws like GDPR can lead to massive fines and legal issues.
Key Steps: Encrypt user data, get explicit consent for data collection, and have a clear breach response plan. Regular audits help ensure compliance.
Practical Developer Tips
Conducting Security Audits
Regular audits are essential for maintaining software security.
- How to Do It: Use a combination of automated scanners and manual code reviews. Document all findings and create an action plan to address vulnerabilities.
Using Version Control and Secure Repositories
Version control keeps track of code changes and ensures only authorized people can access your code. Why It’s Crucial: Secure repositories (like GitHub) allow you to manage who can view or edit the code, providing an extra layer of security.
Leveraging Community Resources
Engaging the Developer Community
Open collaboration can lead to better security practices.
Bug Bounty Programs: Encourage ethical hackers to report vulnerabilities by offering rewards. Many tech giants use these programs to identify issues before malicious hackers can.
Real-World Examples
Success Stories
Highlight companies that have effectively secured their software, detailing what worked for them and why.
Lessons from Failures
Discuss companies that experienced devastating breaches and what Endbugflow can learn from their mistakes.
Conclusion
Protecting Endbugflow software is not a one-time task but an ongoing commitment that involves multiple layers of defense. By understanding how Endbugflow software can be protected, you can take proactive measures to safeguard your intellectual property, secure sensitive data, and maintain your competitive edge. Start with strong legal protections like copyrights and patents to ensure your software is well-defended in court if needed. Use trade secrets to keep crucial parts of your software confidential, and enforce strict licensing agreements to control how your software is used.
On the technical side, secure coding practices, robust encryption, and real-time threat monitoring are crucial. Regular code audits and the use of code obfuscation add layers of security that make it difficult for attackers to reverse-engineer your software. Remember, even the most secure software can be compromised by human error, so invest in user training to make your team a strong line of defense. User-friendly security features like multi-factor authentication can also make a big difference without burdening your users.
Additionally, keeping up with the latest technologies, like AI-driven security measures, will future-proof Endbugflow against new threats. Staying compliant with evolving data privacy laws, such as GDPR and CCPA, ensures that you avoid legal repercussions while maintaining user trust. Don’t underestimate the power of community engagement through bug bounty programs and open collaboration, as fresh eyes can often catch issues you may have missed.
