Google Cybersecurity Certification Overview
Google Cybersecurity certification is an online program designed to help individuals build basic skills in cybersecurity. Google cybersecurity certification program is launched to meet the increasing demand of cybersecurity professionals. This certificate program is best suitable for beginners, who want to grow their careers in cybersecurity without prior experience in Cybersecurity or IT.
What is the Importance of Google Cybersecurity Certification in today’s world?
According to U.S. Bureau of Labor Statistics, the projected growth rate for cybersecurity analyst roles is 35% from 2023 to 20231. Which shows that the demand of cybersecurity professionals will be much high than any other occupation in future.
In this regard, Google Cybersecurity Certification provides foundational skills in cybersecurity and its related fields like information security, risk management and vulnerability assessment. The certificate offers hand-on training with platforms like Linux, SQL and Python, helping students build the competencies that cybersecurity employers seek. Google Cybersecurity Certificate serves as a valuable step toward gaining both knowledge and credibility needed to stand out in a competitive job market.
The Demand for Cybersecurity Professionals and Google’s Cybersecurity Certification Trends
The need for cybersecurity professionals is increasing fast. As more businesses go digital, cyber threats like hacking, data breaches, and ransomware attacks are becoming more common. This has led to a growing demand for skilled experts who can protect companies’ data and systems. According to Cybersecurity Ventures, there will be a 3.5 million unfilled cybersecurity jobs by 2025 2. This highlights the urgent need for qualified professionals in the field.
Why Are Cybersecurity Jobs in High Demand?
Cybercrime is on the rise. Attacks like ransomware, phishing, and identity theft are becoming more frequent, making cybersecurity a top priority for companies. CompTIA reports that in 2023, there were over 700,000 cybersecurity job openings, with a growth rate of 35% . The demand for experts in areas like threat detection, risk management, and network security continues to grow, making cybersecurity one of the fastest-growing job sectors in tech.3
The shift to remote work, the rise of cloud computing, and the spread of Internet of Things (IoT) devices have also increased the need for strong cybersecurity measures. As these trends continue, businesses need more professionals who can safeguard their data and systems from cyber threats.
Google’s Cybersecurity Certification: A Solution to the Skills Gap
To help fill the growing demand for cybersecurity professionals, Google launched its Cybersecurity Certification program in 2021. This program is aimed at people with little or no prior experience in cybersecurity and teaches them essential skills for entry-level cybersecurity jobs.
The program has become very popular, with many individuals turning to it to start a career in cybersecurity. The certification covers important topics like network security, incident response, and system administration. It gives learners the knowledge they need to get started in the field and helps bridge the skills gap in cybersecurity. By offering a low-cost, flexible learning option, Google is helping people enter the cybersecurity job market more easily. According to Coursera, 82% of learners report career benefits after completing Google’s certification, including new job opportunities or career advancement.4
How Google’s Cybersecurity Certification Can Boost Career Growth
Earning a Google Cybersecurity Certification can give you an edge in the job market. Many employers recognize Google’s training as high-quality and relevant to industry needs, making certified candidates more attractive to hiring managers. A 2023 survey by Global Knowledge found that 70% of hiring managers prefer candidates with certifications, including those from google!.5
Which Platform offers Google Cybersecurity Certification?
You can get Google Cybersecurity Certification from at Coursera.org.6 Coursera is an online learning platforms that offers a wide range of courses, certifications, and degree programs. Coursera offers these courses with partnership with Universities and Companies. This platform was founded in 2012 by Daphne Koller and Andrew Ng, and it is considered as the one the leading platform for online education globally. Coursera provides courses across various fields, including technology, business, health, and personal development.
Courses Offered in Google Cybersecurity Professional Certificate Training
There are total eight courses taught in this training program.
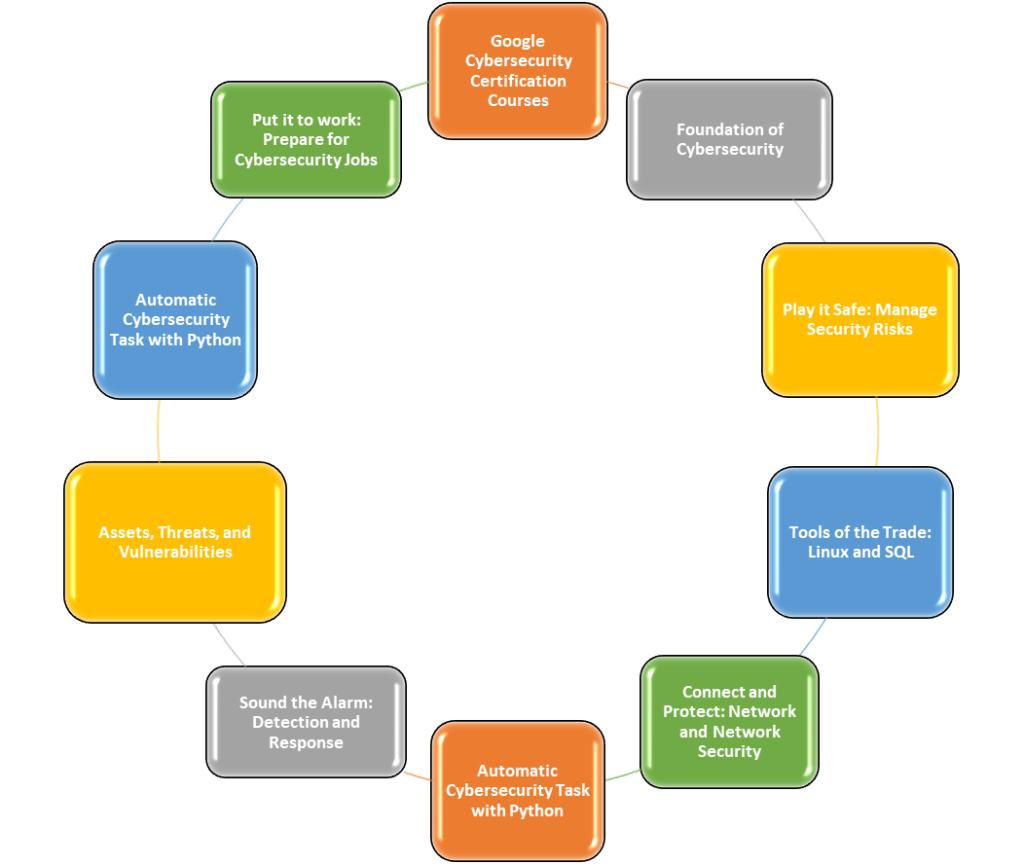
Courses Offered in Google Cybersecurity Professional Certificate Training
- Foundation of Cybersecurity
- Play it Safe: Manage Security Risks
- Connect and Protect: Network and Network Security
- Tools of the Trade: Linux and SQL
- Assets, Threats, and Vulnerabilities
- Sound the Alarm: Detection and Response
- Automatic Cybersecurity Task with Python
- Put it to work: Prepare for Cybersecurity Jobs
1.Foundation of Cybersecurity
| No. of Modules | Review Rating | Experience Required | Schedule Timing | % liking |
| 4 | 4.8 | Beginner Level | 14 hours Approx | 99% |
Foundation of Cybersecurity7 is first of the eight courses in Google Cybersecurity Certification program. This course introduces participants to the fundamentals skills and knowledge needed to start a career in cybersecurity. This course highlights the key competencies that a cybersecurity analyst should rely on, including cybersecurity skills, understanding how security breaches can impact business operations, and the ethical standards which are important for cybersecurity work. Participants also get an introduction to common cybersecurity tools which are used in cybersecurity profession.
Modules of foundation of cybersecurity

- Welcome to the exciting world of Cybersecurity
| 10 Videos | 7 Readings | 1 Quiz | 2 Assignment | 4 Plugins |
- The Evolution of Cybersecurity
| 7 videos | 4 readings | 1 Quiz | 2 assignments | 1 Pugin |
- Protect against threats, risk and vulnerabilities
| 7 Videos | 3 readings | 1 quiz | 2 assignment | 1 plugin |
- Cybersecurity tools and Programming languages
| 5 videos | 8 readings | 2 quizzes | 2 assignments | 1 plugin |
Participants learn useful skills Foundation of cybersecurity course
Cybersecurity: foundational understanding of safeguarding digital assets
Information Security: to protective sensitive information
Ethics in cybersecurity: ethical standards and best practices for responsible cybersecurity work.
NIST Cybersecurity Framework: Structured Guidelines for protecting and responding cybersecurity work.
Historical Attacks: Analyzation of past cyberattacks to understand tactics and strategies.
Real-World Applications
Upon completion, participants will have the skills to evaluate and protect digital assets, implement basic security frameworks like NIST Cybersecurity Framework, and apply ethical hacking principles to safeguard sensitive information.
Career Benefits
Completing the Foundation of Cybersecurity course can lead to entry-level roles in cybersecurity, such as a Cybersecurity Analyst, Information Security Officer, or Network Security Specialist. As the demand for cybersecurity professionals continues to grow, completing this course offers learners a strong foundation for entering the field.
Recognition by Employers
Google’s Cybersecurity Professional Certificate is recognized by top employers like IBM, Intel, and Walmart, making it a credible credential in the cybersecurity industry. According to reviews on Coursera, many learners report securing new job opportunities after completing the certification
2.Play it Safe: Manage Security Risks
| No. of Modules | Review Rating | Experience Required | Schedule Timing | % liking |
| 4 | 4.8 | Beginner Level | 11 hours | 98 |
This is the second course in Google Cybersecurity Certificate Program[3]. This course focuses on identifying, assessing, and managing security risk and vulnerabilities and that an organization can face. This course also teaches about security information and Event Management tools that cybersecurity professionals use.
Modules

- Security Domains
| 10 videos | 5 readings | 3 quizzes | 1 plugin |
- Security Frameworks and Control
| 11 videos | 6 readings | 6 quizzes | 1 plugin |
- Introduction to cybersecurity Tools
| 7 videos | 4 readings | 3 quizzes |
- Use Playbooks to respond to incidents
| 7 videos | 6 readings | 3 quizzes | 2 plugins |
After this course students learn following skills.
Security Information and Event Management (SIEM) Tools: These tools help in detecting, monitoring, and responding to security threats in real-time. Learners will understand how to use SIEM tools to identify potential vulnerabilities and minimize risks to organizational assets.
Information Security: Learn the importance of protecting sensitive business information, whether it’s customer data, intellectual property, or operational plans. Students will understand the best practices for safeguarding this data from cyber threats.
NIST Risk Management Framework & NIST Cybersecurity Framework: Students will familiarize themselves with structured guidelines for assessing and managing cybersecurity risks, helping organizations to create effective risk management strategies. The NIST Cybersecurity Framework is widely used in the industry to help organizations build a resilient security posture.
Security Audits: Learn how to conduct security audits to identify weaknesses in a company’s security systems. By performing these audits, cybersecurity professionals can help businesses improve their security measures and comply with industry regulations.
Incident Response Playbook: Understand how to design and implement an Incident Response Playbook, which is a step-by-step guide that outlines how to respond to security incidents. Having a structured playbook helps organizations react quickly and effectively to mitigate potential damage.
Career Benefits
Completing this course provides a foundation in both security risk management and incident response, two of the most crucial areas in cybersecurity. As cyberattacks grow more complex, professionals who can manage risks and respond to incidents will be highly sought after. This course prepares learners for a wide range of roles, including:
- Cybersecurity Analyst
- Risk Management Specialist
- Security Operations Center (SOC) Analyst
- Incident Response Specialist
3.Connect and Protect: Networks and Network Security
The third course in Google Cybersecurity Certification program covers the essentials of network types. It teaches how data travels through networks, and techniques for network security.
| No. of Modules | Review Rating | Experience Required | Schedule Timing | % liking |
| 4 | 4.8 | Beginner level | 14 hours | 98 |
Modules

- Network Architecture
| 13 videos | 8 readings | 4 quizzes | 2 plugins |
- Network Operations
| 7 videos | 7 readings | 5 quizzes | 1 plugin |
- Security Hardening
| 8 Videos | 11 readings | 7 quizzes |
- Secure Against Network Intrusion
| 7 videos | 7 readings | 5 quizzes | 1 plugin |
Connect and Protect: Networks and Network Security8 enables students to learn following skills.
Skills Developed in this Course
By completing this course, you will gain a solid understanding of how to secure networks and protect data while it’s transmitted across systems:
- Security Hardening: Learn techniques to strengthen your network’s defenses. This includes securing the network’s infrastructure, such as routers, firewalls, and switches, to make it less vulnerable to attacks.
- Network Security: Understand how to protect data while it moves across different networks. You’ll explore various methods to ensure that sensitive information is secure during its transmission, preventing unauthorized access.
- Transmission Control Protocol/Internet Protocol (TCP/IP): Get an introduction to how networks are designed and how they operate using TCP/IP. Learn how this protocol helps to ensure secure and reliable data transmission across the network.
- Cloud Networks: Understand the basics of cloud infrastructure security. Learn how data and applications are secured in cloud environments, ensuring that cloud-based systems are protected against threats.
Why This Course Matters
Network security is a critical skill for anyone interested in a career in cybersecurity. In today’s interconnected world, data flows constantly between devices, companies, and users. Keeping this data secure while it travels across various networks is essential for protecting organizations from cyber threats.
This course lays the groundwork for advanced topics in network security. It gives you a foundational understanding of how networks function and how they can be protected, preparing you for more specialized cybersecurity roles in the future.
Career Benefits
Upon completing the course, you will be ready to take on roles such as:
- Network Security Specialist
- Cybersecurity Analyst
- Cloud Security Engineer
- Network Operations Specialist
These roles are in high demand as companies need professionals who can safeguard their network infrastructures against growing cyber threats.
4.Tools of the trade: Linux and SQL
This course introduces students to essential tools and systems widely used in cybersecurity9. Students learn the roles of operating systems, applications, and hardware along with comparing graphical and command-lines interfaces. Course teaches basics of Linux, its components and distributions.
| No. of Modules | Review Rating | Experience Required | Schedule Timing | % liking |
| 4 | 4.8 | Beginner Level | 26 hours | 98% |
Modules

- Introduction to operating systems
| 9 videos | 7 readings | 4 quizzes | 1 assignment | 1 plugin |
- The Linux Operating system
| 9 videos | 7 readings | 4 quizzes | 4 app items | 1 plugin |
- Linux Commands in the Bash Shell
| 12 videos | 9 readings | 5 quizzes | 1 assignment | 12 app items | 1 plugin |
- Databases and SQL
| 12 videos | 14 readings | 5 quizzes | 1 assignment | 10 app items | 1 plugin |
Skills Developed in this Course
By completing this course, you will develop critical skills used in cybersecurity:
- Command Line Interface (CLI):
Learn to execute tasks on Linux systems using the command line. CLI is a powerful tool in cybersecurity, and mastering common commands will help you automate and streamline cybersecurity tasks. - SQL (Structured Query Language):
Get hands-on experience with SQL, which is essential for querying and managing databases. You’ll learn how to retrieve, manipulate, and store data—skills that are crucial for analyzing and protecting sensitive information. - Linux System Configuration & Maintenance:
Master the basics of Linux system administration. This includes managing Linux servers and network environments—key skills for securing infrastructures and ensuring smooth operation in any cybersecurity role. - Bash Scripting:
Learn to write Bash scripts to automate repetitive tasks. Bash scripting is an important tool in cybersecurity workflows as it helps reduce manual effort, increases efficiency, and ensures consistency in processes.
Why This Course Matters
Linux and SQL are two of the most widely used tools in cybersecurity. Many organizations use Linux servers to host their websites, run applications, and store sensitive data, while SQL is essential for managing and protecting databases. By mastering these tools, you will be equipped with practical, in-demand skills that employers look for when hiring cybersecurity professionals.
This course is an essential building block for anyone looking to pursue a career in cybersecurity. It gives you a strong foundation in managing and securing systems, performing database queries, and automating tasks—all of which are critical for modern cybersecurity professionals.
Career Benefits
After completing this course, you’ll be ready to take on roles such as:
- Linux System Administrator
- Cybersecurity Analyst
- Database Administrator
- Security Engineer
- DevOps Engineer
Mastering these tools can give you an edge in the job market, as many companies rely on Linux and SQL for their operations and need professionals who can manage and secure their systems effectively.
5.Assets, Threats and Vulnerabilities
This course focuses on identifying and managing assets, assessing vulnerabilities, and analyzing potential threats10. Students learn how to classify organizational assets, analyze attack surfaces to locate risks and vulnerabilities. This courses also introduces the threat modeling process to asses risk more effectively.
| No. of Modules | Review Rating | Experience Required | Schedule Timing | % liking |
| 4 | 4.8 | Beginner Level | 25 hours | 98% |
Modules

- Introduction to asset Security
| 10 videos | 9 readings | 6 quizzes | 1 plugin |
- Protect Organizational Assets
| 11 videos | 12 readings | 6 quizzes | 4 app items |
- Threats to asset Security
| 12 videos | 10 readings | 7 quizzes | 2 plugins |
- Vulnerabilities in System
| 10 videos | 11 readings | 7 quizzes |
Skills Developed in this Course
By completing this course, you’ll gain essential skills to help you identify, assess, and manage the critical aspects of cybersecurity, including:
- Authentication:
Learn about authentication models, which help verify a user’s identity and ensure that only authorized individuals can access sensitive systems or data. - Vulnerability Assessment:
Understand how to evaluate system weaknesses and vulnerabilities. Learn how to perform assessments to identify areas that need improvement, reducing the risk of attacks. - Cryptography:
Master the basics of cryptography, including techniques for data encryption and secure communication. These practices are essential for ensuring that sensitive information remains confidential and protected from unauthorized access.
Why This Course Matters
Understanding how to protect assets, identify threats, and address vulnerabilities is at the core of effective cybersecurity. With the increasing number of cyberattacks, organizations need professionals who can manage risks and prevent data breaches. By mastering these key concepts, you’ll be able to develop and implement strategies to safeguard systems, data, and digital assets.
This course prepares you to tackle real-world cybersecurity challenges, ensuring that you can effectively protect an organization’s most valuable resources from cyber threats.
Career Benefits
After completing this course, you’ll be ready to pursue a variety of roles in the cybersecurity field, such as:
- Security Analyst
- Cybersecurity Consultant
- Risk Manager
- Penetration Tester
- Incident Responder
Employers highly value professionals who can assess and manage risks, identify vulnerabilities, and secure organizational assets. This course equips you with the practical skills needed to meet those demands and stand out in the job market.
6.Sound the Alarm: Detection and Response
This course equips students with critical skills in incident detection, response and recovery11. Students learn how to analyze network packets, interpret logs, and understand the syntax and components of intrusion Detection System and Network Intrusion Detection Systems.
| No. of Modules | Review Rating | Experience Required | Schedule Timing | % liking |
| 4 | 4.8 | Beginner Level | 24 hours | 98% |
Modules
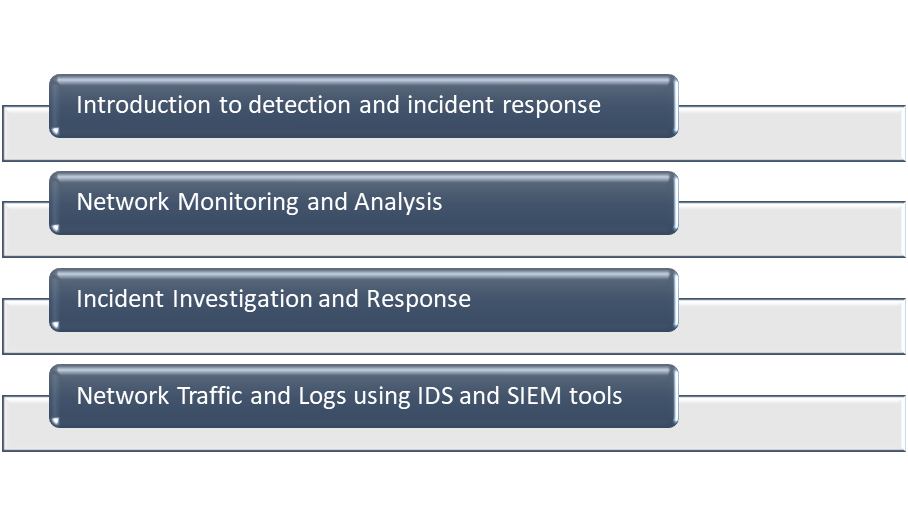
- Introduction to detection and incident response
| 12 videos | 7 readings | 6 quizzes | 1 plugin |
- Network Monitoring and Analysis
| 9 videos | 8 readings | 5 quizzes | 4 app items |
- Incident Investigation and Response
| 11 videos | 10 readings | 7 quizzes | 2 plugins |
- Network Traffic and Logs using IDS and SIEM tools
| 14 videos | 12 readings | 8 quizzes | 2 apps items | 1 plugin |
Skills Developed in this Course
By completing the “Sound the Alarm: Detection and Response” course, students will develop essential skills for detecting and responding to cybersecurity incidents, including:
- Security Information and Event Management (SIEM):
Learn how to use SIEM tools to detect and investigate security incidents. These tools allow you to collect and analyze security data to detect patterns of malicious activity, helping you respond quickly and effectively. - Packet Analyzer:
Gain expertise in analyzing network packets, which are essential for understanding how data moves through a network. Learn how to inspect these packets to identify signs of cyberattacks or unusual behavior. - Intrusion Detection System (IDS):
Understand the role of IDS in detecting unauthorized access or malicious activity within a network. This skill is critical for identifying potential threats before they cause significant damage.
Why This Course Matters
Cybersecurity incidents can happen at any time, and the ability to detect and respond to them swiftly is crucial to minimizing damage and ensuring the security of systems and data. This course provides the essential skills needed to analyze network traffic, use monitoring tools, and investigate potential threats.
Whether you’re an aspiring cybersecurity analyst or looking to expand your skills, this course prepares you for real-world challenges in incident detection and response. You’ll be equipped with the knowledge needed to protect networks and systems from cyberattacks effectively.
Career Benefits
Upon completing this course, you’ll be ready to step into roles such as:
- Cybersecurity Analyst
- Incident Response Specialist
- Security Operations Center (SOC) Analyst
- Network Security Engineer
The ability to detect and respond to security incidents is highly valued by employers, especially with the growing number of cyber threats. Completing this course demonstrates that you have the practical knowledge and skills to handle real-time security issues, making you an asset to any organization.
7.Automate Cybersecurity Tasks with Python
This course introduces students to using python programming12. This course includes basics of python in the context of cybersecurity, application of python inn automates repetitive security tasks and streamline processes. Course also includes practices adhering to the PEP 8 style guide for writing clean, readable code.
| No. of Modules | Review Rating | Experience Required | Schedule Timing | % liking |
| 4 | 4.7 | Beginner Level | 29 hours | 97% |
Modules
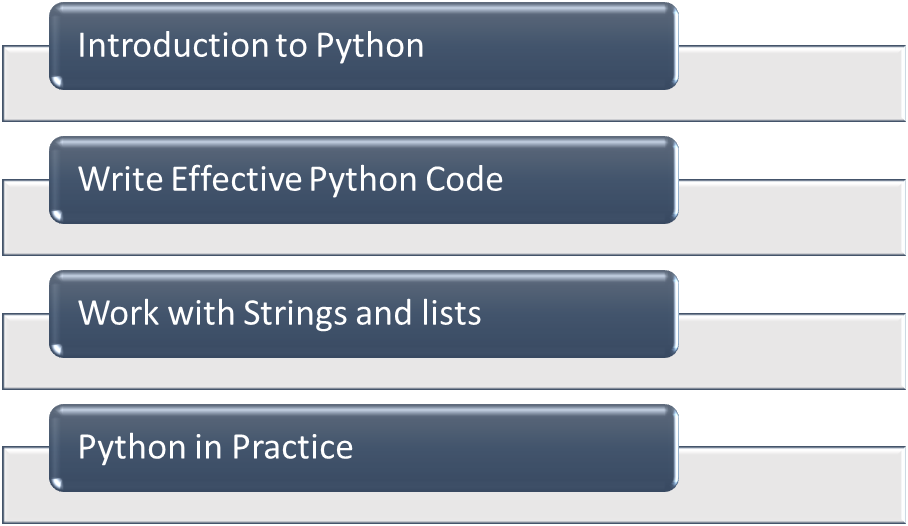
- Introduction to Python
| 12 videos | 11 readings | 3 quizzes | 1 assignment | 8 ungraded labs | 1 plugin |
- Write Effective Python Code
| 10 videos | 7 readings | 4 quizzes | 4 ungraded labs |
- Work with Strings and lists
| 7 videos | 5 readings | 4 quizzes | 6 ungraded labs | 1 plugin |
- Python in Practice
| 11 videos | 11 readings | 5 quizzes | 6 ungraded labs |
Skills Developed in this Course
By completing the “Automate Cybersecurity Tasks with Python” course, you’ll develop essential programming skills to enhance your cybersecurity efforts, including:
- Computer Programming: Gain a strong foundation in programming concepts, which are critical for automating security tasks and building custom solutions.
- Python Programming: Python is a versatile programming language, and learning it will enable you to automate security operations, conduct threat detection, and build scripts for a wide range of security applications.
- Coding: Improve your coding skills to create scripts that automate repetitive tasks such as scanning, monitoring, and reporting.
- PEP 8 Style Guide: Learn how to write professional Python code by adhering to the PEP 8 style guide, which ensures that your code is clean, maintainable, and readable by others.
Why This Course Matters
In cybersecurity, automation is key to staying ahead of evolving threats. Python is a powerful tool that helps security professionals streamline manual tasks and focus on more critical issues. This course provides you with the skills needed to write efficient, automated scripts that enhance the speed and effectiveness of your security measures.
Whether you’re an aspiring cybersecurity analyst, penetration tester, or security engineer, this course equips you with the programming skills to take your career to the next level. Python’s widespread use in cybersecurity makes it a valuable skill for tackling modern-day security challenges.
Career Benefits
After completing this course, you’ll be ready to step into roles such as:
- Cybersecurity Analyst
- Security Automation Engineer
- Incident Response Specialist
- Penetration Tester
With the increasing demand for cybersecurity automation, learning Python programming will make you a highly sought-after professional in the field.
8.Put it to work: Prepare for Cybersecurity Jobs
This is the last course in Google Cybersecurity Certification, this course focuses on preparing students to enter the cybersecurity workforce13. This course prepares students in strong job application preparation and materials like cybersecurity resumes and portfolios.
| No. of Modules | Review Rating | Experience Required | Schedule Timing | % liking |
| 5 | 4.8 | Beginner Level | 19 hours | 99% |
Modules
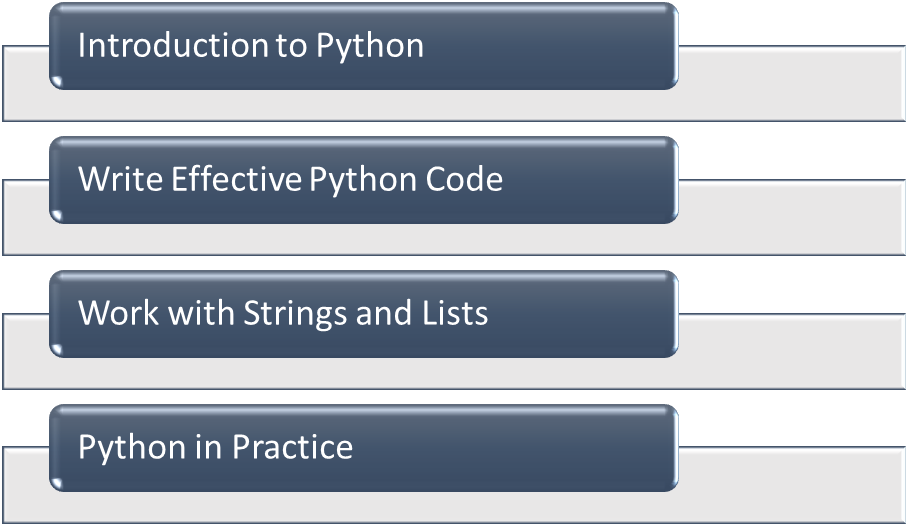
- Introduction to Python
| 12 videos | 11 readings | 3 quizzes | 1 assignment | 8 ungraded labs | 1 plugin |
- Write Effective Python Code
| 10 Videos | 7 Readings | 4 quizzes | 4 Ungraded Labs |
- Work with Strings and Lists
| 7 videos | 5 readings | 4 quizzes | 6 ungraded labs | 1 plugin |
- Python in Practice
| 11 videos | 11 readings | 5 quizzes | 6 ungraded labs |
Skills Developed in this Course
Upon completion of the “Put it to Work: Prepare for Cybersecurity Jobs” course, students will acquire the following skills:
- Escalation Skills: Learn how to effectively escalate security incidents to the appropriate stakeholders to ensure timely and accurate resolution.
- Resume and Portfolio Preparation: Gain the skills to build a professional, standout resume and portfolio that showcase your cybersecurity skills and experience, giving you a competitive edge in job applications.
- Stakeholder Communication: Develop effective communication skills to engage with stakeholders, report incidents, and collaborate on cybersecurity projects.
- Job Preparedness: Understand the job application and interview process, allowing you to confidently navigate applications, interviews, and job offers in the cybersecurity field.
- Integrity and Discretion: Learn the importance of maintaining ethical standards, confidentiality, and discretion when handling sensitive security information, a crucial skill for any cybersecurity professional.
Why This Course Matters
As you prepare to enter the cybersecurity workforce, having the right job preparation skills is crucial. This course provides you with the necessary tools to build a professional image, communicate effectively, and present yourself as a top candidate for cybersecurity roles.
Cybersecurity is one of the fastest-growing fields, and employers are looking for professionals who not only have the technical skills but also the ability to communicate, handle sensitive information, and manage real-world security issues. This course equips you with the competencies needed to launch a successful career in cybersecurity.
Career Benefits
After completing this course, you’ll be ready for roles such as:
- Cybersecurity Analyst
- Incident Response Specialist
- Security Operations Center (SOC) Analyst
- Security Consultant
- Cybersecurity Engineer
Completing this course and earning your Google Cybersecurity Certification will demonstrate to employers that you have the practical skills and professionalism needed to succeed in the cybersecurity field.
What is the procedure to Enroll for Google Cybersecurity Certification?
- To get Google Cybersecurity Certification you have to sign-up at Coursera.org.
Sign-up will require your name, email and password. Put your right credentials and set a strong password.
- Then click on the Enrollment option to enroll in certificate course by entering your name and password.
- Once you enroll the courses, click on each course and start learning.
Entry Level Jobs After Google Cybersecurity Certification
| Job Description | Key Responsibilities |
| Security Analyst | To monitor Organization’s security system for security breaches and help to implement protection. |
| Information Security Associate | To handle basic security administration tasks, like managing access control and supporting senior security team members. |
| IT support Specialist | IT support roles include troubleshooting and managing IT system by eliminating vulnerabilities. |
| Junior Security Operation Center | Junior SOC help to monitor and respond to security incidents and threat detection. |
| Cybersecurity Technician | Setting up firewalls, managing endpoint security and managing antivirus software. |
| Risk and Compliance Associate | To conducts audits, reports on compliance with regulations. |
| Network Security Associate | Monitoring and maintaining of firewalls, configuration of network access and troubleshooting. |
| Incident Response Assistant | To analyze security incidents and prepare reports, working closely with seniors in incident response. |
FAQs About Google Cybersecurity Certification
Is there any Enrollment Deadline for Google Cybersecurity Course?
Google Cybersecurity Certificate enrollment operates regular interval basis. Current Enrollment dates are starting from 10th November 2024 and ends on 30th November 2024.
What is the cost of Google Cybersecurity Certification Course?
Coursera offers 7-days free trial to students, then they have to pay $49/Month Subscription charges.
What is the Minimum quiz passing criteria for Cybersecurity Certificate?
There is no particular passing criteria for certification, but you have to get 80% marks in each course quiz to proceed to next course.
Is there any entry test criteria to enroll in Google Cybersecurity Certification?
No, you can enroll google cybersecurity certification without any prior experience and knowledge and there is no entry test passing criteria.
References:
- https://www.bls.gov/ooh/computer-and-information-technology/information-security-analysts.htm ↩︎
- https://cybersecurityventures.com/jobs/ ↩︎
- https://www.comptia.org/ ↩︎
- https://www.coursera.org/professional-certificates/google-cybersecurity ↩︎
- https://www.globalknowledge.com/en-us/resources/it-skills-and-salary-report/ ↩︎
- https://www.coursera.org/ ↩︎
- https://www.coursera.org/learn/foundations-of-cybersecurity?specialization=google-cybersecurity#recommendations ↩︎
- https://www.coursera.org/learn/networks-and-network-security?specialization=google-cybersecurity ↩︎
- https://www.coursera.org/learn/linux-and-sql?specialization=google-cybersecurity ↩︎
- https://www.coursera.org/learn/assets-threats-and-vulnerabilities?specialization=google-cybersecurity ↩︎
- https://www.coursera.org/learn/detection-and-response?specialization=google-cybersecurity ↩︎
- https://www.coursera.org/learn/automate-cybersecurity-tasks-with-python?specialization=google-cybersecurity ↩︎
- https://www.coursera.org/learn/prepare-for-cybersecurity-jobs?specialization=google-cybersecurity ↩︎
